My presentation for this year is Threat Modeling. My first stop is the 2024 Palmetto Cybersecurity Summit Feb 21-22, 2024, in Columbia SC. I’ll also be speaking at BSides Nashville May 11, 2024, and ShowMeCon May 13-14, 2024.
Getting Started
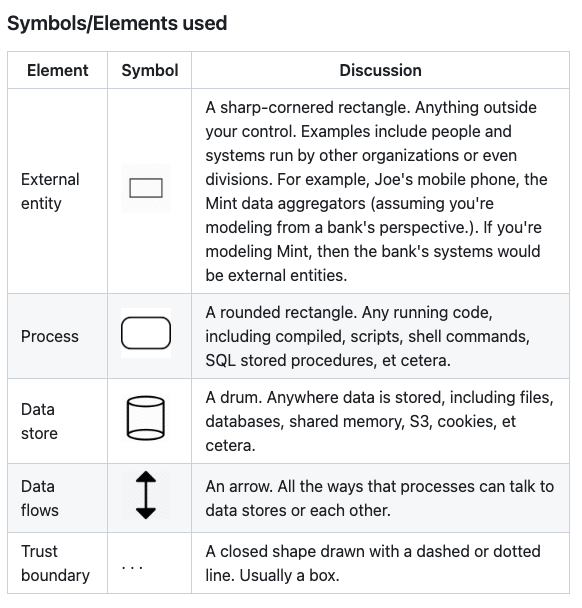
We’re going back to kindergarten people! We’ll get to draw shapes and lines and use different colored markers! To get started all one needs is a whiteboard and markers. Building out a diagram is the first step. As I mentioned in the Basics of Threat Modeling blog post having one prepared prior to the session will help expedite the process. Unfortunately, if there isn’t an existing diagram one will have to be done during the session. Adam Shostack has a description of the symbols and elements to use in a threat model on his GitHub page. They’re very simple and that’s the intention because threat modeling an application or process can get very complex.
Adam Shostack - DFD3 - https://github.com/adamshostack/DFD3
If the session is virtual and not in person the same principles applies. All popular video conferencing has a whiteboard feature on it that can be used for threat modeling. There are third-party options as well including:
Microsoft Whiteboard (Usually free with corporate account)
Microsoft Visio (License required)
OWASP Threat Dragon (Free)
Draw.io (Free)
Miro (Free version)
Lucidchart (Free version)
MURAL (Free version)
Whimsical (Free version)
The tools I’ve had experience with are Microsoft’s Whiteboard, Visio, and Threat Modeling Tool. Visio and the Threat Modeling Tool get into a lot of detail and can feel complex if you’re just getting started. The more important thing is learning the methodology and approach to threat modeling. Threat Dragon has a lot more simplicity. It is open-source so doesn’t have all the bells and whistles of other tools. It can take a little to get used to using. I’ve seen developers create diagrams with Draw.IO. It’s simple and easy to use but be mindful that if they build it on a third-party website they may be putting internal organization information on the internet. I have not used Miro, Lucidchart, MURAL, or Whimsical but they look similar to Draw.IO. Leave a comment below with your favorite white boarding tool.
Automated threat modeling tools
I have only used Microsoft Threat Modeling Tool and OWASP Threat Dragon for automating parts of the threat model process. Microsoft’s Threat Modeling Tool get’s very granular and tries to be exhaustive on attack scenarios. If you like digging into a lot of details it can be a very useful tool. OWASP Threat Dragon is a much lighter version of that which is why I used it a lot more. For me I wanted the group to come up with their own attack scenarios because it allowed them to exercise their security muscles and build a stronger security mindset. This impacts the other areas of their day-to-day work. As their working they’ll be thinking about security.
There are other commercial and open-source tools that promise one-click threat modeling. I have not had an opportunity to use them. Here are some popular ones I found:
If you have used one of these or another leave a comment below.
Educational Resources
The book I always recommend is Threat Modeling: Designing for Security by Adam Shostack. It is “THE” book on threat modeling. What I love about the book is that after the first chapter it says to just start threat modeling. It’s more of a companion book for learning and maturing the threat modeling program.
OWASP is another resource for threat modeling. They have an entire project on everything you need to know about Threat Modeling. The OWASP Cheat Sheet is also a great place to start and a good reference point while maturing the threat modeling practice. Finally, an exhaustive list of threat modeling resources can be found at Awesome Threat Modeling on GitHub.
Leave a comment below with resources or tools you recommend. If you’re interested in seeing a version of this talk check out the ColaSec Meetup page as I will be presenting on threat modeling at the February 20th, 2024, meetup. A virtual option for attending is available.