In the ever-evolving landscape of cybersecurity, threat modeling emerges as a crucial practice that helps organizations identify, assess, and mitigate potential security threats. It's a proactive approach that focuses on understanding the assets that need protection, identifying what threats those assets might face, and defining measures to mitigate those threats. Here are some essential tips and best practices for effective threat modeling:
1. Start Early and Integrate Continuously
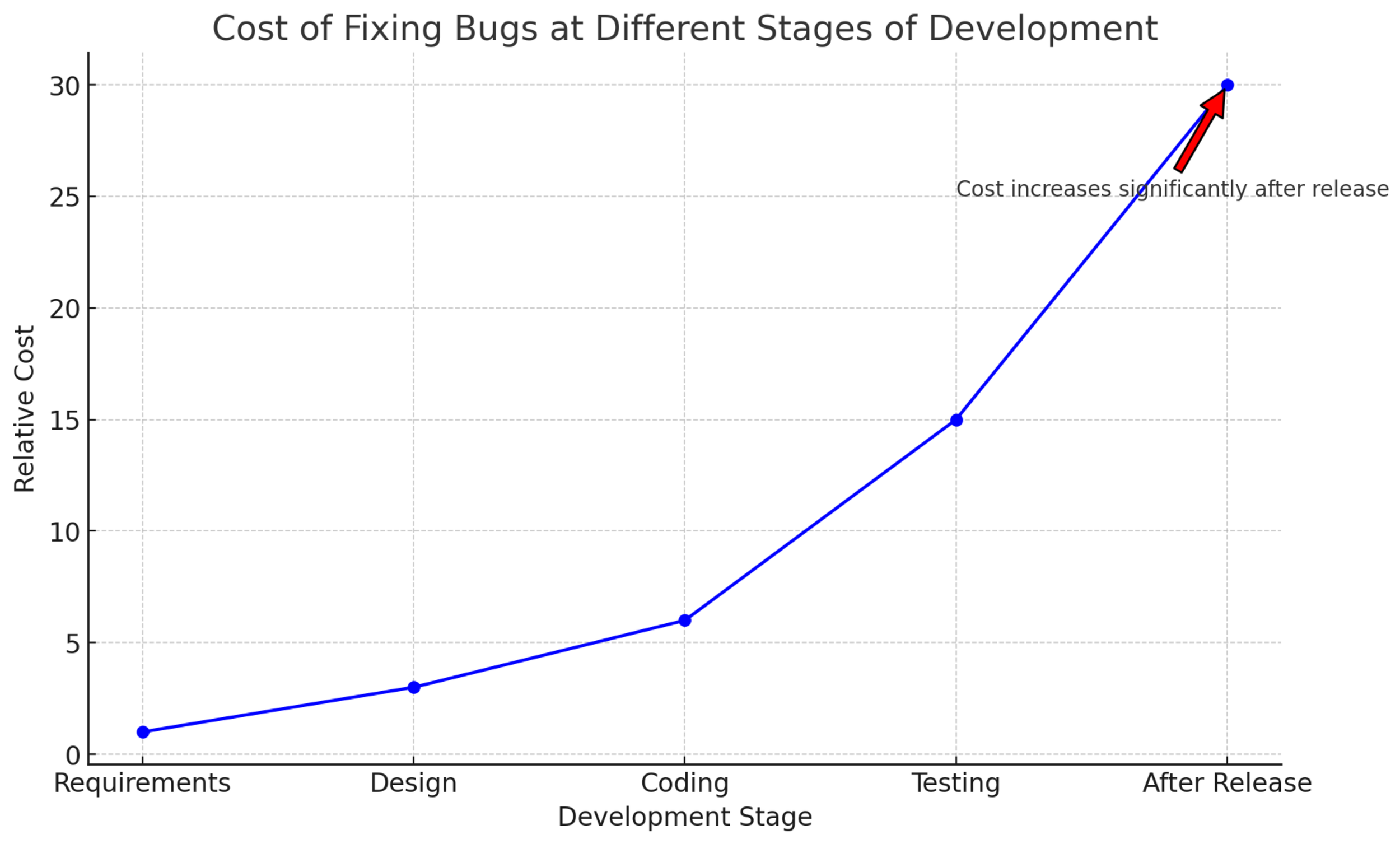
Begin threat modeling at the earliest stages of system design and continue to integrate it throughout the development lifecycle. Early integration helps in identifying potential security issues when they are easier and less costly to resolve. Studies has shown the fixing issues later in development or IT project are more costly.
A chart showing the cost of fixing a bug throughout the development lifecycle
2. Involve a Cross-Functional Team
Threat modeling should not be the sole responsibility of the security team. It requires a collaborative effort involving developers, operations, architects, and business stakeholders. Each group brings a unique perspective that contributes to a comprehensive understanding of the system and its potential vulnerabilities.
There are other benefits to threat modeling outside of security. It get’s everyone involved in the project on the same page. Often development and infrastructure teams can be at odds about what needs to be done to complete the project. Threat modeling is an opportunity to bring everyone together to better understand and clarify what needs to get done.
3. Watch for scope creep
Identify what is being discussed at the start of the session. This will help setup boundaries for the discussion. People will want to dive into are other topics adjacent to the project. While they may need to be discussed at some point now is the time to discuss what was defined in the scope. I often will tell people let’s setup another session or move the discussion to later in the meeting if there’s time. This will help the meeting run more smoothly and ensure the topic of discussion get’s threat modeled.
4. Keep the Attacker's Perspective Simple
Thinking like an attacker can provide invaluable insights into potential vulnerabilities and attack vectors. Understand the capabilities, motives, and methods of potential attackers to better anticipate and counteract their actions. Not everyone has an attacker mindset. Most people in an organization are builders. We as attackers are looking to tear things down and break them.
This can take some getting used to for people. It may take multiple sessions before they start getting into the attacker mindset. It’s a lot like exercise. It takes time to build up those security muscles but once it happens it will make the meeting run a lot more smoother. I often start with simple attacks such as offering someone a million dollars for their access.
5. Use silence
As I’m drawing out a diagram, I will often be thinking of attacks. This isn’t necessarily the case with people outside of security. Especially, if threat modeling is new to them. If I provide all the attack scenarios it won’t help the others in the room foster that security mindset. Use silence to get people engaged in the discussion.
Most people are uncomfortable in a group setting with silence. The facilitator of the session will need to get comfortable with silence. After a period of time someone will speak up with an idea. Don’t shoot down all ideas. Write them down like you would a brainstorming session. This will help encourage more people to speak up with their ideas.
6. threat modeling discussions are chaos
If it feels like chaos you’re likely doing it right. As you go through the session you may feel like you’re taking a step back and adding things to the diagram or the security profile. That’s okay. Keep your eraser tool handy because you may need to adjust different things on the diagram. I’ve been in sessions that I thought were going to take 20 minutes and they ended up taking three hours.
7. Meeting notes and action notes
Identify someone to help take notes. This will with more thoroughly document the meeting. Governance Risk and Compliance (GRC) folks are great at this. After the meeting ask for the notes to compare with your own. Virtual meetings can be recorded for later viewing and ensuring notes are complete.
After the meeting send the meeting notes, a picture or screenshot of the diagram, and action items. This will help document the meeting and allow anyone to make corrections on the notes. Action items are important for any follow up items that need to be addressed. Make sure to identify a person to follow up with and not a group. Also, it doesn’t hurt to document these in a central repository that everyone can access.
Conclusion
Threat modeling is an essential practice in the toolkit of cybersecurity professionals. Threat modeling sessions can often feel like chaos and that’s okay. Make sure to start early and integrate into development and IT projects. Involve anyone that has work to be done as part of the process. Watch for scope creep and offer to set up another time to discuss. Use silence and keep the attacks simple to get people engaged in the conversation. Finally, remember to document each discussion, assign action items, and give people the opportunity to make corrections on the topic discussed.
Threat modeling is one of the low cost and most effective tools in your organization. These tips and best practices will ensure that threat modeling being performed at an organization will be efficient and effective. Leave a comment below if you have any tips or best practices for threat modeling.